We live in an era where hackers are trying anything and everything to obtain your details. With an army of bots at their disposal it is now more important than ever to be aware of malicious emails, phishing, and spoofing attempts.
So, Before We Begin, What Is Phishing Exactly?
Phishing is when someone pretends to be a person or an organisation that you trust, and they exploit this trust to gain privileged information from you such as your passwords or bank details. For example, an attacker can send you an email claiming to be from your bank, asking that you ‘log in’ so that your account could be verified. When you click on the login link in the email, instead of logging in to your bank, you end up sending the attacker your user name and password which you entered into the fake login page.
This gives the attacker enough information to do whatever they want with your account.
Majority of spoofing emails disguise themselves as coming from secure and known sources such as banks and building societies, major retailers, social media giants, and other popular websites. It is very common for the subject line of the incoming email to create a sense of urgency and panic – encouraging that you open the email and take action.
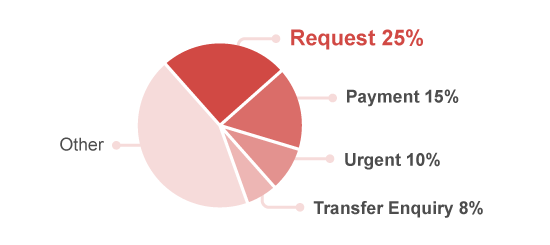 Source: Symantec Government Report
Source: Symantec Government Report
The sender’s domain will often be disguised as a legitimate-looking email address to deceive you into thinking that the message originated from the company that the attacker is phishing. In addition, the ‘From’ name can be disguised with aliases like ‘My Bank’ as opposed to the actual bank name to make the message look authentic.
If you think a message might be fake, you should check the message headers along with the IP address of the sender to see if you recognise it. Sometimes, attackers might even go as far as including a padlock image in the subject line or even in the template itself to convince the recipient into thinking that the message is legitimate.
In our previous post we wrote about the importance of setting up three Domain Name Service (DNS) records to ensure best deliverability of emails; the Reverse DNS, Sender Policy Framework (SPF), and DomainKeys Identified Mail (DKIM) help to increase your email deliverability and provide verification of your identity as the sender. While you’re at it, why not check out our handy email marketing terminology summary here.
Although many companies spend time and effort to mount defences against malicious emails; carefully calibrating email filters and firewalls to protect your inbox from receiving rogue, malicious messages, unfortunately these defences aren’t always enough. According to the 2017 Internet Security Threat Report by Symantec about 1 in 2596 emails is a phishing attempt, according to the report, targeted phishing (known as spear phishing) continues to grow with many high-profile cases such as the hacking of the emails of Hillary Clinton campaign chairman John Podesta.
Top Tips
While the techniques for attacking innocent internet users may sound advanced and intimidating, there are a number of simple ways to protect yourself from becoming the victim of phishing.
From Name
The most common phishing attempts are carried out by changing the ‘From’ address name field, in many cases the attacker will pretend to hold the address of a reputable organisation. Look out for spelling mistakes or unusual domain names in the ‘from’ address for example ‘@a.mazon.com’ rather than ‘@amazon.com’ as this is the most common phishing technique deceiving users into thinking the email is from a secure source and therefore safe.
Do Not Click
This is a general rule of thumb for any internet citizen; if you are unsure what it is, or it doesn’t look quite right – do not click it! It is always best to be cautious of unfamiliar emails that arrive into your inbox, especially if they contain an attachment as this can result in viruses not only damaging your computer, but also spreading through your network and affecting other devices (as was the case with the famous ransomware WannaCry). So, be very suspicious of new emails and never click on unknown messages or download attachments from them.
Spelling
A common characteristic in many phishing emails is the spelling. Regular spelling and grammar mistakes are a strong indicator of malicious emails, those are often accompanied by ‘spammy’ words such as ‘free’, ‘profits’, ‘no fees’ etc.
No Personalisation
Receiving ‘important’ emails without a personalisation field should be a natural warning sign, it shows that the person emailing you does not have any of your details and could potentially be a spammer attempting to phish you. You should be wary of emails like this, as emails from reputable sources will always have some form of personalisation.
Requesting Personal Information
Ever had emails come through requesting you to provide your bank details? These messages are a prime example of phishing emails. Firstly, banks and reputable companies would never ask for personal details especially via email, any personal information about you can usually be accessed and updated via your account with the company in a safe and secure manner.
Subject: Urgent!
Subject lines containing a sense of urgency are a clever social engineering trick designed to push users to take action quickly, especially if the email contains phrases and words akin to ‘your account has been suspended’. These trigger a sense of panic and cause users to make mistakes and not investigate the message properly often falling into a trap.
Always ensure that the message is legitimate before taking any action, even if it calls for urgency.
No Email Signature
In most cases, when someone emails you their message will contain some form of signature, nine out of ten times the signature will contain company information such as the persons’ contact details, phone numbers, websites, and social media thus clearly linking to the company itself. You should be wary of emails which lack any further contact details of the sender.
Fake Logos and Poor Structure
In attempts to make a phishing email look legitimate, spammers will attempt to employ images such as brand logos or design elements, however often they are too lazy to use a high-quality image and resort to a distorted or pixelated version of a company’s logo.
They might also attempt to mimic the layout of a legitimate message by attempting to place header and footer content, you should be very cautious of such details and never engage with a message if it looks different from the usual content you receive from a company.
Tackling Phishing with Campaignmaster
At Campaignmaster we understand the damage phishing can cause not only to end users, but also legitimate companies who use email for marketing; we work tirelessly with our clients to ensure that their emails are marked as safe and legitimate messages. Our dedicated team tirelessly monitors the health of the individual IP addresses we assign to each client to ensure that they are not being blacklisted which is one of the potential signs of an address being used for phishing.
Moreover, as standard, all self-hosted clients are equipped with DomainKeys Identified Email (DKIM) and Domain-based Message Authentication, Reporting & Conformance (DMARC) records to ensure that the emails are being properly authenticated and verified against established records allowing provides to block suspicious activity and protect you from mail-related attacks. You can read more about the importance of these authentications in email marketing deliverability here.
Sender Policy Framework (SPF) is yet another way in which emails can be authenticated as coming from a legitimate source, the SPF signature is verified against public record to prove that the email is authorised by the organisation.
During account setup, our team checks all records to ensure that our clients’ messages are marked as legitimate get delivered safely to their destination.