An email is a communication that is sent from one server (email clients) to another (receiving email servers). Whilst an email is in transit from one server to another, it becomes vulnerable as it is open for unknown parties to eavesdrop on.
TLS or Transport Layer Security helps stop this from happening by encrypting the email whilst it is in transit.
Essentially, TLS is an encryption protocol which protects data as it is sent between computers in order to facilitate communications security over the internet. Professional email services, such as Campaignmaster, support TLS (most commonly TLS 1.2).
Older versions being 1.0 and 1.1 have been deprecated by major browsers and so it is important to upgrade to at least 1.2. It is also just as important to disable older versions.
When talking about TLS, there are two key concepts you should understand. These are as follows:
- TLS uses PKI (Public Key Infrastructure) to encrypt emails. Each public key used to encrypt an email has a respective private key. This respective private key is used to decrypt. Encrypting emails in this way makes it more difficult for email communications to be intercepted by unknown parties.
- TLS uses digital certificates to authenticate receiving servers, ensuring the receivers are legitimate. The authentication of sending servers is optional.
How does TLS work?
Now that you know the two key concepts associated with TLS, it’s time to delve into how it actually works.
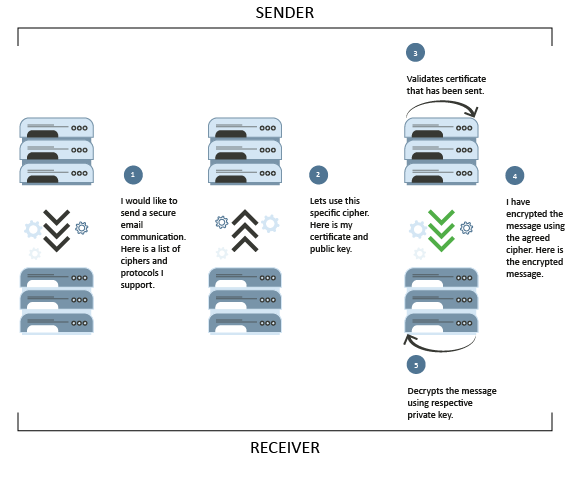
Let’s say you are trying to send an email to a client. The first thing that will happen is the sending and receiving email servers involved will make contact over an SMTP (Simple Mail Transfer Protocol) connection. The sending server will then send a STARTTLS command to the receiving server to request the more secure TLS connection.
If and when the receiving server approves the TLS connection, a list of ciphers understood by the sending server is sent across to the receiving server.
The receiving server will then proceed by selecting a cipher it too understands, whilst also sending back its security certificate and public encryption key.
The sending server will then verify this certificate to ensure the receiving server is legitimate (which is concept number two described above). Once verified, it will use the public key to encrypt and send the email communication. The receiving server has the only respective private key that can be used to decrypt the email (which is concept number one described above).
This process is illustrated below:
Sending emails with TLS
When it comes to sending emails, you will usually have the option to adopt opportunistic TLS. This means the servers will attempt to create an encrypted connection but if this is not possible for any reason, the email will be sent unencrypted.
In cases where you know for definite a domain you are sending an email to supports TLS, you can generate a rule that demands a TLS connection, meaning the connection will drop (email will not be sent) if the sending and receiving server cannot agree on an encryption method.
For our clients, we enable opportunistic TLS as standard in all accounts. We can enable forced TLS if required, on top of all the other deliverability measures we offer.
Receiving emails with TLS
Ideally, when receiving emails, opportunistic TLS should be enabled. As with sending emails, you can also generate a rule that demands a TLS connection when you are certain the sender supports TLS, meaning any emails not using a TLS connection will be rejected.
If you are not sure if a TLS connection is being used, you can check the headers of the email. If TLS is being adopted, you should see something like “version=TLS1_2” followed by the cipher used.
Reaching the inbox is imperative for an email marketing company and one of the main reasons why many professional firms turn to Campaignmaster for their email marketing needs. Get in touch at info@campaignmaster.co.uk for more details on our services.